Authentication
To access the HTTP-API your client must first login to M/Monit. The form based authentication process used by M/Monit is the same as the one specified in the Java Servlet Specification.
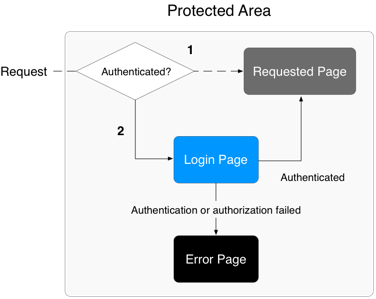
1. Upon access to a protected area the M/Monit server determines if the client has been previously authenticated, if this is the case, the requested page is sent back to the client.
2. If the client has not been authenticated, the M/Monit server stores the original request URL and displays a login page. The client posts a login form back to the M/Monit server and the server attempts to authenticate the user credentials embedded in the form. If authentication fails the server returns an error page. If authentication succeeds, the server checks if the authenticated user belongs to a security role that is authorized to access the requested page. If the user is authorized the server redirects the request to the original stored request URL. If the user is not authorized to access the requested page the M/Monit server will send a 403 Forbidden response back to the client.
Form Based Authentication utilizes HTTP session and clients must support cookies and send the session cookie, zsessionid, with every request.
If the session timed out or is invalidated, the user is logged out and any subsequent request requires the user to re-authenticate.
CSRF-Protection
M/Monit protect against Cross-Site Request Forgery (CSRF) attacks by using a scheme called Double Submit Cookies. In short, this means that M/Monit requires that the authenticated session cookie is submitted with the request as usual, but that the value is also repeated in either a request parameter or in a HTTP header, of which an attacker cannot replicate as they cannot read the cookie.
If you use M/Monit’s HTTP-API from your own program, CSRF might not be a concern. If this is the case, use the z_csrf_protection parameter during login and set it to off in which case CSRF-protection will be turned off. Otherwise, you must read the CSRF-Token from M/Monit’s session API and submit the token in a HTTP header or as a request parameter with each POST request to /admin/
Examples
See the cURL example for more details